Federal networks are under constant cyberattack from adversaries that range from young hacktivists looking to make a point — and a name — to organized criminal groups interested in financial gain and terrorist activities.
But, according to researchers at the Government Accountability Office, the biggest threat to the government's most high-impact systems comes from nation-state sponsored hackers and groups.
Download: Agencies Need to Improve Controls Over Selected High-Impact Systems
This was readily apparent last year, when the Office of Personnel Management discovered hackers — widely attributed as associated with the Chinese government — had breached a database holding highly sensitive information on more than 21.5 million Americans.
Similar high-impact systems exist throughout the government, classified as systems that would have a "severe or catastrophic adverse effect on organizational operations, organizational assets or individuals" that would render the agency unable to meet its mission.
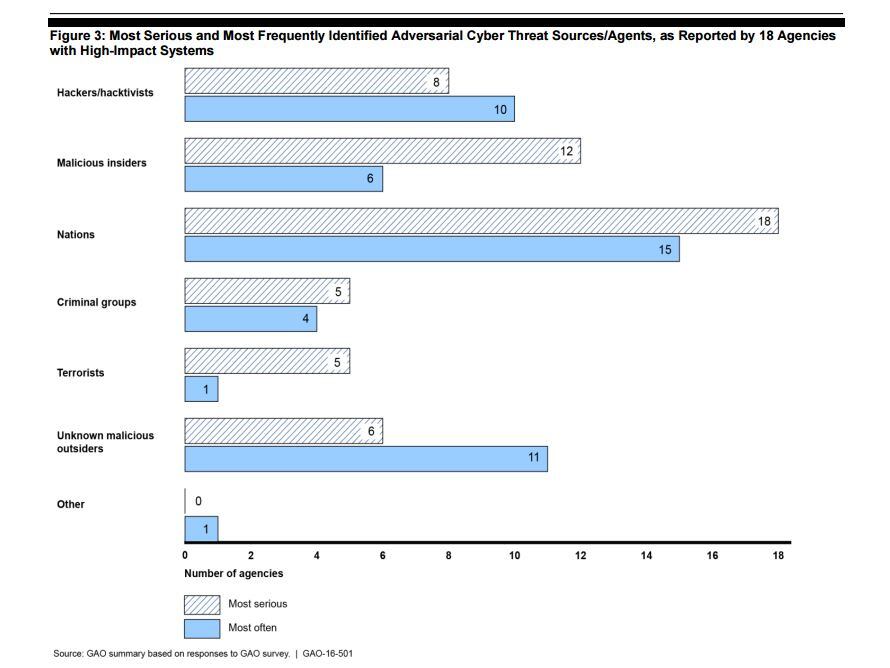
According to the GAO, of the 24 major agencies, 18 had high-impact systems, which accounted for 9.4 percent of the government's 9,714 systems in 2015.
GAO analysts spoke with officials at all 18 agencies and discovered that nation-state actors are both the most frequent and most serious threat to federal networks.
For "most serious," malicious insiders and hacktivists came in second and third, respectively; unknown malicious outsiders and hacktivists were the second and third most frequent groups, respectively.
The majority of these nation-state groups are focused on gathering information on the U.S. government — what is generally called traditional espionage. Much of that is allowable under international norms, though that doesn't mean agencies shouldn't do everything possible to keep their systems and data secure.
"Our high-impact systems contain sensitive information that we cannot afford to have breached by outside groups," said Sen. Tom Carper, D-Del., ranking member of the Senate Homeland Security and Governmental Affairs Committee. "While our defenses are getting stronger, these attacks are getting more sophisticated."
There's nothing unique about nation-state malware, as Joshua Pitts, director of security research at NopSec, demonstrated at last year's Black Hat conference.
"Nation-state weapons really are not special or magical — they're just developed in private," Pitts said while dissecting a complicated piece of malware developed by a Russian-sponsored group.
While there was nothing in the code that couldn't be replicated — and, in fact, had been many times over — the power behind nation-state hacking groups are the resources provided by those nations, which can be considerable.
And there's no end in sight.
According to the GAO, citing data reported to the U.S. Computer Emergency Readiness Team (US-CERT), the number of cyber incidents affecting federal networks increased by 1,303 percent in 10 years, jumping from 5,503 in 2006 to 77,183 in 2015.
The GAO has specific recommendations for a number of agencies, though most boiled down to updating security plans and improving continuous monitoring capabilities.
"Foreign nations continue to work to penetrate federal networks and information systems to access our government's sensitive information," said Homeland Committee Chairman Ron Johnson, R-Wis. "I remain concerned that federal agencies are not fulfilling their responsibilities under the law to secure federal information systems. Our committee is asking agencies to respond to these findings and will monitor progress to ensure that federal agencies follow the law and take adequate precautions to protect sensitive information."
Aaron Boyd is an awarding-winning journalist currently serving as editor of Federal Times — a Washington, D.C. institution covering federal workforce and contracting for more than 50 years — and Fifth Domain — a news and information hub focused on cybersecurity and cyberwar from a civilian, military and international perspective.